DigitalResidue's Forensics: Malware Incident Response pt. 2. (Collecting Volatile and Non-Volatile data)
Por um escritor misterioso
Descrição

2016년 18주차 정보보안 뉴스클리핑
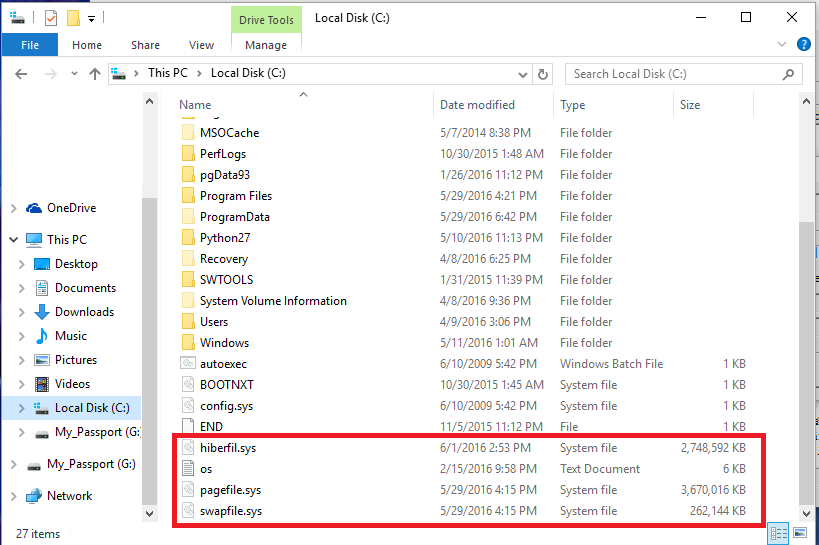
DigitalResidue's Forensics

008 Collecting volatile data part1 : Windows Forensics
TryHackMe — DFIR: An Introduction, by exploit_daily

Memory Forensics for Incident Response

17.2- Performing Incident Response - Part 2 (Managing Data Sources for Incident Response Lab)
Windows Volatile Memory Acquisition & Forensics 2018, Lucideus Forensics, by Lucideus

Volatility Popular and Open Source Memory Forensics Tool

Analyzing Memory Dumps — R2D2 Malware, by ka1d0
de
por adulto (o preço varia de acordo com o tamanho do grupo)